Cloud capabilities are continuously increasing from the past few years, and this has gained momentum over the COVID-19 pandemic period. However, organizations are confronting major security risks of cloud computing that are likely to further increase in 2022 if proper safety mechanisms are not put in place.
Organizations often treat the security of cloud resources separately from the security of on-premises resources. However, increased attacks on cloud resources, including taking advantage of compromises in on-premises security for lateral attacks on the cloud, necessitate the integration of on-premises and cloud security.
This also includes enhancing the security of private and public cloud resources that are accessed more during the COVID-19 pandemic period.
Here, we’ve listed what are the security risks of cloud computing that are likely to continue to heighten through 2022. Organizations must pay heed to these risks, to detect, prevent, and respond to cloud attacks.
Top Security Risks of Cloud Computing
1. Data Breaches and Data Leaks

When information or data gets extracted or leaked without authorization, the condition is called data breach. In most data breaches, attackers try to extract usernames, passwords, email addresses, names, and credit card numbers.
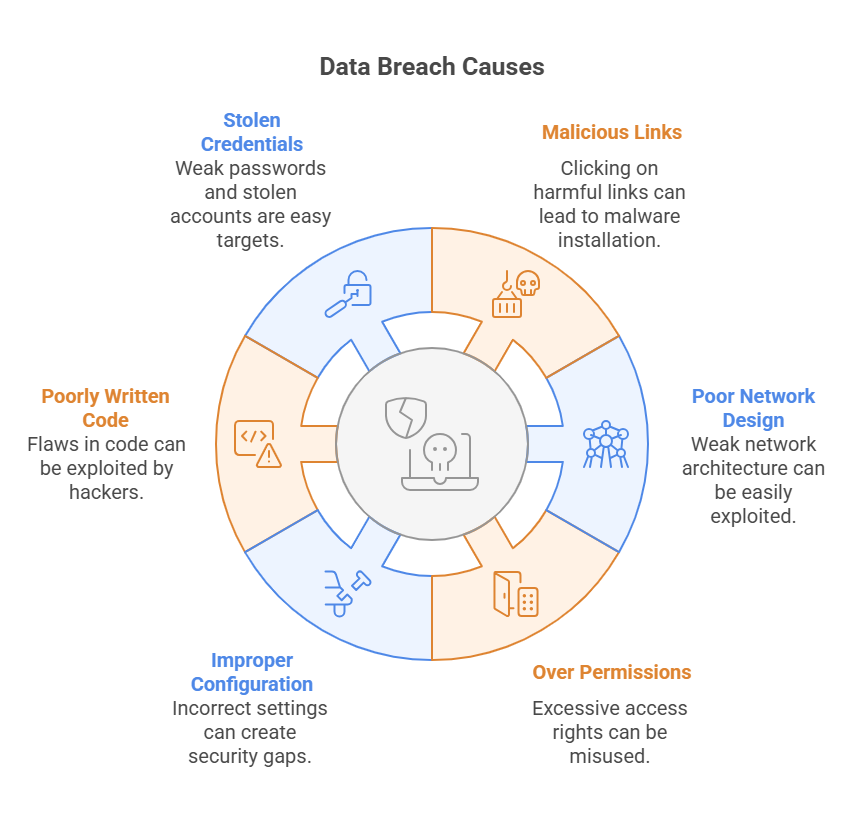
Data breaches occur in the following ways:
- Malicious link and software
- Badly designed network
- Over permissions
- Improper configuration
- Applications with poorly written code
- Stolen and weak credentials
As per the IBM study on “Cost of Data Breach” done by Ponemon Institute, more than 500 organizations faced data breaches over the period of May 2020 to March 2021.
How to Prevent Data Leaks and Data Breaches
There are multiple approaches to identify user activity in the cloud security system, which include:
- Multi-factor Authentication: In this approach, the user needs to provide more than his/her username and password. When the user enters the password and tries to log in, he/she receives a randomly generated, single-use pin on his/her mobile that remains active for a short period of time. Multi-factor authentication has emerged as a vital cloud security standard to protect data.
- Data-at-Rest Encryption: In this approach, data is stored in the system, but users can’t use it on other devices frequently. This process involves datasets, logs, databases, and more.
How AWS Addresses Data Security Concerns
Amazon Web Services (AWS), a leading cloud services provider, has the highest level of data security and privacy. AWS allows you to build applications on the most secure infrastructure, where you always own your data, and have the ability to move it, encrypt it, and manage retention.
All data moving through the AWS global network interconnecting the AWS regions and datacenters is encrypted automatically at the physical layer, before leaving the secured facilities of AWS. Further encryption layers also exist, for example, service or customer-to-service TLS connections, and all VPC cross-region peering traffic.
The security solutions and services of AWS aim to provide the following key advantages. These advantages help you implement optimal security for your organization, and minimize the risk of data leaks and data breaches.
Prevent: Define user identities and permissions, data protection and infrastructure protection measures for a planned and smooth AWS adoption strategy.
Detect: Get visibility into the security posture of your organization with monitoring and logging services. Store this information in a scalable platform for testing, auditing, and event management.
Respond: Get automated incident response and recovery from shifting the focus of security teams from response to analysis of the root cause.
Remediate: Leverage event driven automation for quickly remediating and securing your AWS environment in near real-time.
2. Loss of Visibility
Multiple companies access various cloud computing services through different departments and devices. Such complex setups of cloud services lead to the loss of visibility of access to cloud infrastructure.
Not being able to access the right procedure can cause one to lose sight of the cloud service. It can also damage the uploading and accessing of data. The risk of data loss and data breach can be eliminated by seeing the cloud storage’s online visibility.
The loss of visibility happens due to the following reasons:
- Non-alignment of security architecture with the business objectives and goals
- Un-updated threat models
- Not employing continuous monitoring capability
How to Prevent Loss of Visibility?
Taking frequent backups is one of the effective ways to secure data from loss of visibility. Create a schedule for taking timely backups and clear separation of necessary data to be backed up, and the unnecessary data can be deleted. You can secure and detect unauthorized backups by employing data loss prevention (DLP) software.
Organizations can also geo-diversify backups and encrypt their data to prevent data theft or loss. Offline data backup is also an effective way to deal with ransomware.
3. Lack of Secure Application User Interface (API)

In the cloud, API helps to maintain control. Some APIs are built in mobile applications or on the web to allow access by an external user or a company employee.
Any external API can invite unauthorized access by attackers intending to access an organization’s confidential data as well as manipulate services. Such external-facing APIs increase cloud security risk.
Following are the reasons behind API security risks:
- Inadequate logging and monitoring
- Improper asset management
- Broken function level authorization
- Insufficient resources and rate limiting
- Security misconfiguration
- Excessive data exposure
- Broken authentication
How to Prevent Insecure API
To prevent insecure application user interfaces, developers need to design them with strong encryption, access control, and authentication. This can increase the security of APIs.
Implementing penetration tests can also help secure external attacks targeted to API endpoints and attain a preventable code review.
It’s best to have a secure SDLC (Software Development Life Cycle) to build secure software as well as APIs. Making use of SSL/TLS encryption for data-in-transit as well as implementing multi-factor authentication with schemas like one-time passwords, digital identities can help reinforce API security.
4. Misconfigured Cloud Storage
A survey by Accurics, “State of DevSecOps”, outlined that misconfigured cloud storage services present in 93% cloud deployments resulted in more than 200 breaches, exposing over 30 billion records. Hence, this is one of the most noteworthy cloud security risks that you need to deal with seriously.
There is an increase in misconfiguration of cloud services with the rising complexity in services. This cloud security risk can lead to damage in the stored information or data with public data exposure, data deletion, or data manipulation. The following reasons cause misconfiguration:
- Incomplete IAM configurations and weak password policy
- Firewall rules allowing public-facing traffic
- Forming storage buckets with public access
- Databases with improper security settings
How to Prevent Misconfigured Storage
For securing misconfigured data, you need to cross-check the cloud security configurations by establishing a dedicated cloud server. You can store it safely and can keep the contents in it safely.
Find the security configurations with the help of specialized cloud solutions and tools, which can also analyze the state of these security configurations and detect potential issues before anything goes wrong.
5. Shadow IT

Cloud shadow IT involves cloud services engagement by individual employees, departments, or other entities of an organization outside the change management and IT security processes.
The primary reason behind this risk in cloud security is managers getting tired of waiting for IT to address business needs. Monitoring controls, policies, and procedures don’t exist or aren’t effective enough to detect and manage the issue.
Surpassing IT and security review, the shadow IT services may face common cloud vulnerabilities, like weak authentication, weak or nonexistent overall risk assessment, and lack of proper data restrictions.
How to Manage Shadow IT
Managing shadow IT is a bit difficult as it’s not just a technology problem; it can also be accompanied by political baggage.
Shadow IT emerges because it’s perceived that IT is not responsive to the business needs. Business managers often have goals they must meet, and the unresponsiveness of IT causes them to seek other ways to get the tools they need. They tend to contract cloud services beyond the standard change management and SDLC procedures.
To manage shadow IT, the first step is establishing a good working relationship between the business and IT. It’s also important to have policies specifying the results of using resources or engaging in services that didn’t go through the documentation and approval steps that ensure secure operation as well as constant attention to threat management and vulnerability.
Moreover, organizations need to monitor for any unapproved use of cloud resources. There are several solutions that accomplish this. In their budgets for 2022, organizations should include the TTP required to employ the right solution.
Amazon Web Services (AWS) allows its customers to customize a version of AWS Marketplace, which enables employees to find pre-approved software products. This significantly reduces the risk of shadow IT for companies.
Wrapping Up
Switching to the cloud calls for taking comprehensive cloud security measures for protecting important data and mitigating the cloud security threats. Businesses need to put strong cloud security policies in place that should be integrated into the IT processes, which teams employ for building applications and deploying the cloud infrastructure.
Businesses must address the security risks of cloud computing continuously while utilizing appropriate security tools to make operational work more manageable and more convenient. With the right technology and approach, businesses can tap into the potential of cloud computing, in a safe and secure way.
AQB Solutions helps businesses with powerful cloud security solutions, which can ensure the security of workloads and critical data, facilitating business continuity. We are an AWS Select Consulting Partner, and have the resources and expertise to set up robust AWS cloud infrastructure for businesses as well as perform highly secure cloud migrations.
We leverage the security solutions of AWS to minimize cloud security risks and ensure the highest level of security for our customers’ cloud infrastructure. If you’ve security concerns in cloud computing, consider talking to one of our cloud experts today!

