The U.S Congress initiated and passed the HIPAA (Health Insurance Portability and Accountability Act) in 1996. According to the latest amendment made to the policy, the HIPAA regulations are majorly dedicated to improvising the aspects of data security.
These regulations protect the ePHI, i.e. electronic protected health information, and the CSP, i.e., Cloud Service Providers, by heightening the security.
The New HIPAA regulations primarily impact the healthcare sector. As per the new regulation passed, the CSP’s of these healthcare organizations are eligible to undertake the responsibilities of their BA’s (Business Associates) only upon complying with specific HIPAA regulations.
The regulation lays down an elaborate guideline that needs to be followed by every organization of the industry for data protection in the cloud servers. These guidelines are needed to improvise the control the organization would have over the data system access, thereby making it close to impossible for any malfunctioning or data breach to occur.
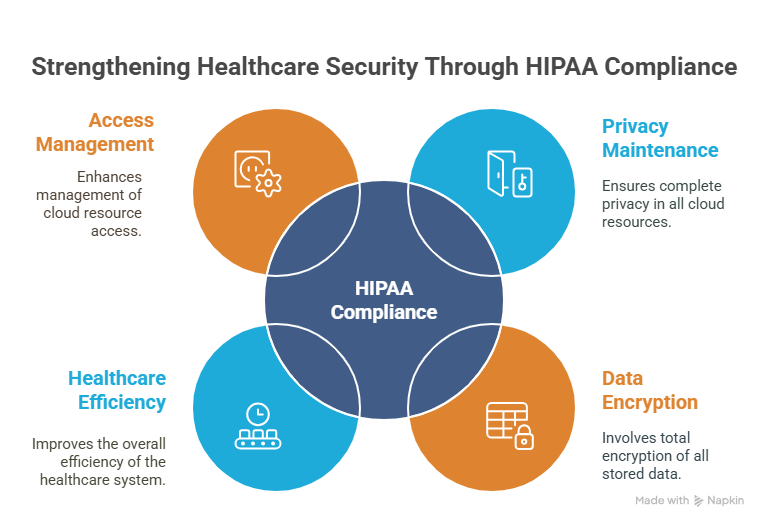
Compliance with HIPAA ensures certain aspects, which are as follows:
>Ensure complete privacy maintenance in all the cloud resources
>A total encryption of every data stored in the cloud
>Improvise the overall efficiency of the healthcare system
>Enhanced management of cloud resource access for both the administration and customers
Healthcare organizations, being the most highly regulated industry; need to maintain connectivity on all enterprise-use devices. This connectivity can be achieved effectively by implementing Enterprise Mobility Management.
Password Management:
The organizations need to enforce strong password policies. Users must be guided to keep passwords, which are a combination of upper case, lower case, numbers, and special characters.
This password security can easily be monitored and taken care of by having a dedicated IT admin to emphasize Enterprise Mobility Management effectively. HHS recommends that file-sharing applications must be prevented on Enterprise-use devices to prevent any sharing of customer data using file-sharing applications.
Top-notch EMM providers create dedicated work containers on every employee device to prevent any file syncing or sharing misusage.
Updated Security and Encryption Technology:
As per new HIPAA Regulations, during the exchange of data through mobile devices, enhanced data protection needs to be implemented. Big data encryption technology is implemented to achieve data protection.
There are various levels of encryption available, which could help to improve data security both while the data is at rest or in the transfer. Only an EMM provider dedicated to keeping up-to-date with technology would be able to understand and implement the highest data encryption.
Using an Enterprise-grade solution is a mandate for an IT admin to have better oversight of devices inclusive of sensitive information access.
Device Connectivity:
Healthcare organizations are recommended to ensure that every employee maintains physical control over the enterprise-use devices at all times. This control would help EMM-based IT admins to obtain a real-time report of all the connected devices.
Such connectivity would provide the admin with the complete control to track the location and activities of every connected device, thereby ensuring maximum security of sensitive data. Additionally, once any enterprise-use device becomes outdated or no longer in use, it should be ensured that all sensitive patient information is wiped clean, before it is discarded.
Using a well-developed EMM, an IT admin could efficiently perform these tedious tasks of wiping off data and restoring it to factory settings, with complete ease.
The Final Verdict:
As per the privacy rule, an advanced Enterprise Mobility Management technology could help to ensure that no entity can access sensitive ePHI. They ensure enhanced security with full compliance to HIPAA industrial and privacy policies.




